

An update on the state of cyber-security in 2024 – Ransomware, QR code ‘quishing’, and more
28 Jun 2024, by Slade Baylis
Every six months or so we like to do a review of the state of cybersecurity in the IT landscape. It’s rarely good news, with cyberattacks seeming to only ever grow in number and in frequency. And unfortunately, this month’s news is not much different.
In this month’s article, we’ll be discussing the trends that we’re seeing so far in 2024, and make you aware of what things to look out for in the new financial year. We’ll touch on the increase of the number of ransomware attacks targeting healthcare organisations, and the reasons behind why it’s happening. We’ll discuss QR code phishing scams, explaining what they are and how to avoid them. And we’ll also talk about how things are shifting more towards identity-based attacks, rather than malware-based ones.
Ransomware attacks on the rise, yet again
Following the successful breach of Change Healthcare earlier this year, other cybercriminal groups have taken notice and responded to it by increasing the number of attacks against healthcare providers. This shouldn’t come as much of a surprise, as the 22-million-dollar ransom payment from Change Healthcare was the second largest ransomware payment in history. With this sort of money being injected into the ransomware “market”, it was inevitable that this would incentivise other malicious actors to adjust their behaviour accordingly.
For those not across it, a ransomware attack is a type of cyberattack wherein malware – malicious software – infects a device and then steals and encrypts all the data on it. The cybercriminal will then offer to sell the keys needed to decrypt the data to the victim, often requesting exorbitant fees to be paid in cryptocurrency.
As reported by Wired1, Allan Liska, a threat intelligence analyst from the cybersecurity firm Recorded Future, said that their firm tracked 44 cases of cybercriminal groups targeting healthcare organisations with ransomware attacks. “That's more health care victims of ransomware than in any month Recorded Future has seen in its four years of collecting that data" he said. Whilst it’s impossible to definitively prove that the increase was as a result of the Change Healthcare breach, Liska noted that it was unlikely to be a coincidence.
On a more positive note though, it appears that ransomware attacks in general are down when compared with previous years. As reported by Sophos2 in their State of Ransomware 2024 report, they found that – of the 5,000 IT and cybersecurity leaders that they surveyed – 59% of them were hit with some form of ransomware last year, which is a 7% drop from the two years prior. Whilst any drop is welcome, 59% is still a high rate and we highly recommend organisations still continue to actively take measures to defend against it.
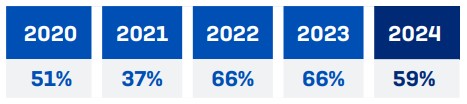
Source: Sophos, State of Ransomware 2024, Rate of Ransomware Attacks
The growing threat of physical QR code phishing attacks
As if cyberthreats in the digital world weren’t enough! Unfortunately, now another form of attack that has been growing in number is the rise of QR code phishing attacks – also known as “quishing”. Potentially related to the drastic increased use of QR codes following the covid pandemic, with them being used to simplify the act of “checking-in” to a location, the malicious tampering of publicly displayed QR codes is now something that everyone will need to be conscious of.
We’ve seen QR codes used before in emails to obscure links to what would otherwise be obviously malicious links, but it’s the use of these sorts of attacks in the real world that’s concerning. As announced by Crime Stoppers Victoria3, one common tactic used by these malicious actors is to place stickers with their own QR codes over the top of otherwise normal QR codes used by restaurants, venues, and other organisations.
One example they gave was from speaking to a recent quishing victim. In the example, the victim scanned a fake code from what they believed to be a standard menu whilst at a gathering with friends. The problem was that a clear sticker had been placed over the top of the legitimate QR code, which instead took them to a website where he was asked to fill in his personal and financial information. As this was their first time to the establishment, it didn’t seem out of the normal, and so they filled it in and provided all the data that was requested.
It’s due to how easy this scam is to fall for that we recommend not using QR codes in locations that you don’t trust. However, even if you do, it’s worth double-checking the code to ensure it hasn’t been covered with a sticker or tampered with.
Other forms of this attack have been to send packages to potential victims with malicious QR codes on them, or to send mail asking for donations to a charity or cause. For defending yourself from these forms of quishing attacks, look for typos and spelling mistakes in the information you receive or the URLs/links that you are sent to once you’ve scanned the QR code. You should also be cautious if any site asking you to provide sensitive information or grant access to your phone, location, microphone, or any other features after you’ve scanned the QR code.
Malware-free identity-based attacks represented 75% of detections in 2023
With the defence against malware getting better and better on the prevention side, as EDR (Endpoint Detection and Response) and behaviour-based detection services improve, many attacks have now switched to faster and more effective means of breaking in, which is that of “identity-based” attacks.
Identity-based attacks are ones that don’t look to utilise malware to break into systems, but rather target individuals. This can include phishing, social engineering, or initial access brokers. Access brokers are the relatively new kid on the block, however they have become a key component of the cybercrime landscape4. Instead of more typical cybercriminals that look to break in and immediately compromise systems - initial access brokers instead look to steal credentials or break into systems, and then they sell access to what they've broken into to third parties. Whilst this can be less lucrative than other forms of attack, such as ransomware, it can also be less prone to detection and thus less risky for the access broker.
With regards to phishing specifically, we’ve touched on the threat of these sorts of attacks before in our own article on phishing. In that article, we talked about the many different types of phishing attacks that exist, as well as their increasing sophistication. For those interested, we recommend checking out that Deep Dive: What is phishing, where did it come from, and how can you avoid it article for more information on it.
What’s been particularly interesting though, according to Crowdstrike5 – a leader in the cybersecurity space – is that malware-free activity represented 75% of detections in 2023, up from 71% the year prior. The reason given for this (in their 2024 Global Threat Report) was the success of these forms of attack, and also the introduction of the previously-mentioned access broker services.
Have any questions about these new threats or how to protect yourself against them?
If you have any questions about these new cybersecurity developments, or just want to discuss how to improve your security posture, please let us know!
We’re happy to perform an audit of your systems, processes and infrastructure. Being the experts in secure cloud, we can provide guidance on how you can improve your protection against cybersecurity threats - from the traditional ones right through to new and emerging threats.
Sources
1, Wired, “Medical-Targeted Ransomware Is Breaking Records After Change Healthcare’s $22M Payout”, <https://www.wired.com/story/change-healthcare-22-million-payment-ransomware-spike/>
2, Sophos, State of Ransomware 2024, <https://assets.sophos.com/X24WTUEQ/at/9brgj5n44hqvgsp5f5bqcps/sophos-state-of-ransomware-2024-wp.pdf>
3, Crime Stoppers Victoria, “Decoding QR Code Scams” <https://www.crimestoppersvic.com.au/events/decoding-qr-code-scams/>
4, ABC News, “Initial access brokers are the latest cybercriminals targeting Australians. Here's how they work”, <https://www.abc.net.au/news/2024-04-06/initial-access-brokers-cybercrime-hacking-data-breach/103617306>
5, Crowdstrike, “Global Threat Report 2024”, <https://www.crowdstrike.com/global-threat-report/>
