

Optus, Medibank, and now Harcourts – If they can be breached, what can you do to prevent it?
29 Nov 2022, by Slade Baylis
When you hear news about large organisations being hit by a new data breach that has exposed the private information of millions of people, it can be hard not to be disheartened as a smaller business. With the recent news of the Optus, Medibank, and Harcourts data breaches - with the private information of millions of Australian citizens being released - one can't help but think, if such highly reputable Australian organisations with large IT budgets aren’t able to prevent this sort of cyber-crime, what chance does a smaller fish have?
Whilst it’s not much consolation to those who’ve had their data stolen, for others who are worried about the possibility of getting hacked themselves, there is a silver lining. The fact is, that in each of these cases, it was something that was easily preventable which was the cause of the compromise – this means that if smaller organisations are vigilant, by first establishing sensible security policies and then sticking to them, then they can remain protected from these sort of attacks.
In this article, we’ll go into some background on each of these attacks, explain the attack vector that was used, and then list the lessons that each of our customers can learn from this in order to help prevent themselves from falling victim to these same sort of attacks.
Optus – The compromise of private information for over ten million customers
When it comes to the most serious data breaches in recent memory, it’s hard not to list the recent Optus breach amongst the top. Not only is the number of customers affected – over 10 million – incredibly large, but the information that was stolen was personal information which will reduce the reliability and security of verification processes that other organisations all over Australia use.
The information that was stolen included names, physical addresses, email addresses, phone numbers, and dates of birth – even worse still, for some customers the information included identification numbers such as driver’s licence, Medicare and even passport numbers. Due to the incredibly sensitive nature of this information, this data breach has downstream effects on the security of other services that these affected customers use. The full ramifications of this is best explained by the fact that this sort of personal information is often used by organisations to verify that the person they’re speaking to over the phone is actually who they claim to be. If malicious third-parties have access to this information, then this could enable a huge range of further attacks, such as Optus’ customers becoming victims of identity theft down the line.
Due to this serious and unfortunately likely threat, state and federal governments have responded by making it easier for those affected to replace identity documents that may have been compromised during the breach. Not only that, but as reported by The Guardian1, the federal government is now looking at urgent reform in this area – which includes making it easier to alert banks as to which of their customers may have been compromised, as well as looking at potential fines for companies that allow such a breach to occur in the first place.
The attack vector for this data breach is worth knowing about - as the alleged cause of the breach is not something as sophisticated as most would assume. As reported by the ABC2, a senior figure inside Optus gave confidential insights into the early findings uncovered by the telecommunication company’s IT specialists, under the condition of anonymity. Whilst Optus has officially rejected that human error was a contributing factor in the breach, according to this insider, the cause of the breach appeared to come down to an improperly secured API endpoint.
Simply put, an API (Application Programming Interface) is an interface that is used to allow different software components to communicate and share information with each other. By utilising APIs, companies can allow other systems to access, modify, and remove information, or even access functionality via a documented interface. The benefits of APIs are great and they are used across the internet, with most of the popular apps available today utilising them extensively. For example, any weather app on your phone will request information from the Bureau of Meteorology to get live updates on a moment-to-moment basis - something that would be impossible without an API connection. However, in any API implementation, it’s important to make sure that proper authentication and access control mechanisms are in place.
According to the insider, the data breach was caused by Optus’ customer identity database being accessible via an API that was open to their internal systems. The insider said that Optus "wanted to make integrating systems easier, to satisfy two-factor authentication regulations from the industry watchdog, the Australian Communications and Media Authority (ACMA)”. Whilst initially this endpoint was not accessible to external systems due to network segregation, it’s alleged that at some point the API became exposed to a test network that had full internet access.
In a reply to ISMG3, the Information Security Media Group, the person going by the alias “Optusdata” - who claimed credit for the attack and is the one who posted the original ransom demand of one million dollars - posted a message about how the attack took place. This alleged attacker claimed that the API endpoint was completely open with bad access control, not requiring any form of authentication to access the data.
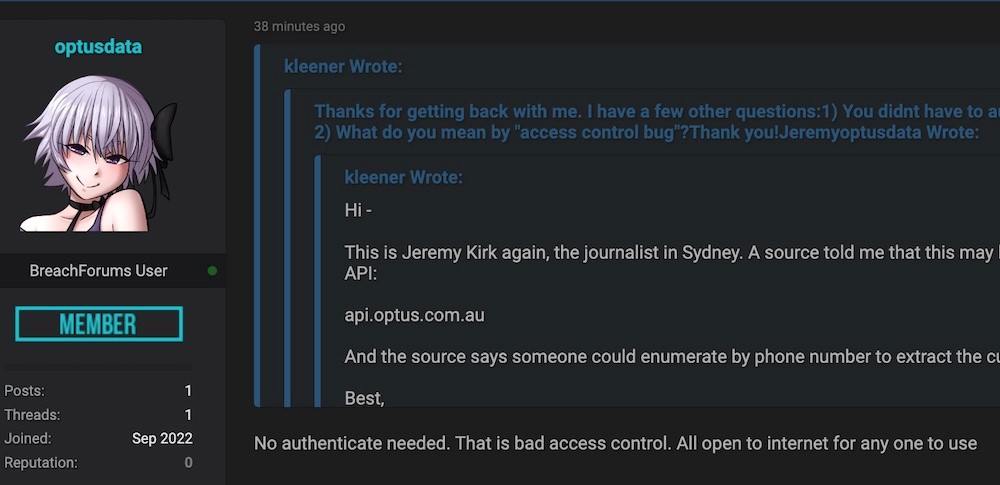
If these allegations are true, then the data breach is anything but sophisticated – with an API endpoint being open to the internet, one would only require the knowledge that it was accessible in order to steal customer data. Due to how easy the attack was to perform, many hackers, on the same forum where the ransom was posted, were noted as criticising the breach.
As reported by MSN4, one user noted that “Optus probably would have legit paid you a lot to quietly plug the leak. No too smart. If your gonna data steal at least don't be an amateur”. Others criticised the attacker as “stupid”, “not very professional”, and called them a “script kiddie” – which is an unflattering term used by the community to refer to someone who uses prebuilt software to perform cyber-attacks, often without having any actual knowledge about how they work.
This unflattering term may be more apt than intended, as some have pointed to the quick withdrawal of the one-million-dollar ransom and panicked responses from “Optusdata” after the attack gained national attention as potential evidence of the attacker being underage. It wouldn’t be the first time either, as earlier this year the BBC5 reported on two teenagers (16 and 17) who appeared at the Highbury Corner Youth Court in London, charged with a number of cyber-offences. The two were both arrested as part of investigation into the “Lapsus$” gang, who are responsible for a number of different cyber-attacks against large tech companies, including Microsoft, Nvidia, and Samsung.
What can we learn from the Optus breach? Don’t assume your systems are secure
Overall, the primary lesson that businesses watching this unfold can learn is not to assume that applications are secured though the configuration or protections built into the environment. In the case of this Optus attack, fairly standard authentication and access-control features were absent from the API, likely due to the perceived lack of risk as the system was only accessible via internal/private networks.
The problem with this assumption is that a fairly innocuous change in the future could cause a nightmare for the organisation and their customers. From a networking point of view, adding a public network to a system could be seen as a fairly safe task – a networking engineer might assume that any hosted applications would necessarily be built to restrict access to data and systems, and thus underestimate the risk or potential damage of such a change. However, in this case, it looks like assumptions around who could and couldn’t access the system resulted in the API being improperly implemented, which in turn lead to it being exposed to malicious actors.
Due to this, it’s important to make sure that all systems are implemented with proper authentication and access-control protection, regardless of other protections that are in place to limit who can access those systems at an environment or infrastructure level.
Medibank - The compromise of private information for up-to five hundred thousand customers
With the scale of the Optus attack, with over ten million customers having had their data stolen, one could be forgiven for being less concerned at the scale of the Medibank attack - with just under five hundred thousand customers being affected. However, it could be argued that this cyber-attack is even more serious due to the nature of the data that was stolen.
Whilst the Optus data breach included personally identifiable information - the data that was exfiltrated from insurer Medibank, arguably included more sensitive information such as details on service provider names, as well as information associated with patient diagnoses and procedures. The insurer has said that overall, health claims for about 160,000 of its Medibank customers, 300,000 of its ahm customers, and 20,000 of its international customers were accessed – bringing the total to nearly 500,000 customers all up.
As reported by HealthTech6 - Tom Kellermann, Chief Cybersecurity Officer of Carbon Black, said that “Health information is a treasure trove for criminals” … “by compromising it, by stealing it, by having it sold, you have seven to 10 personal identifying characteristics of an individual”. With more sensitive and private information, not only do you have a similar potential for identity theft, but in addition criminals can leverage it by coercing and extorting their victims into doing what they want them to do. Due to this increase in perceived value, stolen medical data usually has exponentially higher “street value” than other more innocuous forms of information.
Whilst this information is often used for the same ultimate end - which is a financial payoff - in these instances, it's often the customers themselves who get targeted directly in follow-up attacks. These additional attacks can cause customers to suffer further stress and potentially even impact their mental health. Hence, it’s due to the serious nature of this breach that the federal government is taking action to not only track down the culprits, but to also prevent further similar attacks in the future.
Unlike the Optus breach, where the attack is suspected to have been committed by a single individual, in this Medibank case, the attack has been confirmed to have been committed by a Russian hacker group. As reported by the ABC7, AFP Commissioner Reece Kershaw confirmed criminals based in Russia had been identified as the culprits behind the Medibank hack. In addition, Cyber Security Minister for Home Affairs, Clare O'Neil, along with Attorney-General, Mark Dreyfus, announced the formation of a joint cyber police task force. This new joint operation, made up of around 100 officers across the Australian Federal Police (AFP) and the Australian Signals Directorate, has be designed to target online criminals - with Ms O'Neil specifically stating that it will “day in, day out, hunt down the scumbags who are responsible for these malicious crimes against innocent people."
One aspect of this attack that appears to be similar to the Optus breach is the simple nature of the suspected attack vector. The Saturday Paper8 has reported that in private briefings to other companies, Medibank revealed that the criminals “found the login credentials for a single support desk worker at the health insurer that did not have two-factor authentication” … and used that to gain “access to virtually the entire contents of the company’s business.”
Two-factor authentication is a now a common security process that is used to increase the likelihood that a given person is indeed who they say they are. This is achieved through a requirement that users provide two different authentication factors before they are given access to an application or system. For example, a common implementation is to require the user to use their regular login credentials in conjunction with an authentication app on their phone before they are able to log in. This requirement to provide two different authentication factors in order to be able to log in, dramatically increases the security of the systems they have access to.
What can we learn from the Medibank breach? Implement and stick to your security policies
Similar to the lessons learnt from Optus, the lessons with the Medibank breach are also relatively straight forward and simple to implement. The initial attack vector for the Medibank breach appears to have been through the lack of a simple and standard security policy that should have been implemented for all their staff – if two-factor authentication was enabled for all their staff, it’s unlikely the attack would have been possible.
For organisations looking to make sure they don’t become the next national headline, implementing industry-standard security policies and being stringent on compliance will be the best tools in their arsenal.
With regards to compromised user accounts, other protections can and should also be implemented to reduce the risks of such attacks. Having security policies regarding the regular changing of user passwords, reviewing the access levels that staff have ensuring they are restricted to only have access to what they need to do their job, and having extensive off-boarding procedures – all these can help secure you from this sort of threat. On top of this, organisations can implement additional security services that can be used to detect vulnerabilities before they are exploited, help train staff on how to be more vigilant against phishing, as well as detect intrusions to systems by monitoring them for suspicious activity.
Harcourts - The compromise of private information from their rental property database
Although the scale of the attack has not been confirmed, Harcourts has confirmed that a data breach occurred at their Melbourne office in October, potentially exposing the personal information of tenants, landlords, and trades to malicious third-parties.
The information that was potentially stolen was similar in nature to the information stolen in the Optus breach, including names, addresses, email addresses, phone numbers, photo identification, signatures, and bank details. It wasn’t confirmed by Harcourts if any information was actually stolen, just that the data had been accessed by an unauthorised third-party. However, if stolen, this information could open up their customers to potentially being victims of identity theft in the future.
As reported by the ABC9, Harcourts has claimed that the data breach stemmed from their service provider STAFFLINK, a real estate support agency, where the account of one of their employees was allegedly compromised and accessible by third parties. In the email that was sent out to the clients of Harcourts Melbourne City, they said that they were "still investigating the incident but understand it has occurred through an employee using their own device for work purposes rather than the usual (and more secure) company-issued device”. In a response to this allegation, STAFFLINK told the ABC that it was not at fault for the breach and that it had engaged in a meeting with Harcourts about the incident.
One key takeaway from this incident for some has been to shine a light on what information real estate agencies are keeping about their tenants and landlords. In an interview with SBS News10, James Clark, from Digital Rights Watch, said that due to the high demand for properties in Australian cities, “renters feel they don't have a choice but to answer the ‘invasive’ questions - due to not feeling like they have a meaningful choice but to hand over whatever information that is being asked of them because of the fear of not getting the rental”.
In a later interview with ABC9, James Clark responded to the Harcourts breach specifically - "We've been warning about this for a while that the real estate industry has been collecting far too much information, especially about renters," Mr Clark said. "We have no oversight into how long they're storing that for and what else they're doing with that information," he said. "Harcourts was quoted recently as saying that their digital security is top notch, and unfortunately I think it's quite embarrassing that they are the real estate agency that has had this breach."
With the amount of information that’s being collected by those in the real estate industry, breaches like the one seen at Harcourts have almost become a matter of “When will the next attack take place?” rather than “Will a new cyber-attack succeed?”. It’s for this reason, that many are looking to the federal government for regulation about what information should be allowed to be kept by these agencies – limiting the damage if such an attack were to occur again in the future.
What can we learn from the Harcourts breach? It’s important to have control over your IT infrastructure
Whilst there are conflicting claims about the source of the Harcourts breach, if Harcourts is to be believed, then the source of the breach was a staff member's personal device that was compromised. If this is the case, then this highlights the problems with using personal devices whilst working remotely. Not only does this introduce issues with privacy, but it also makes controlling and managing the devices next to impossible for workplaces.
With large amounts of the Australian workforce having moved to a hybrid-model of working remotely part time - making sure work devices are secure and up-to-date has never been more important. As these devices will not necessarily be used on networks that are managed by the IT professionals that control the company network, solutions need to be implemented to monitor and manage these devices remotely. For example, if a staff member is using a personal device to perform their work on - this level of control is next to impossible, dramatically increasing the likelihood of this type of attack.
It’s for this reason that it is important that businesses provide work-owned devices to staff that are expected to work remotely – not only that, but it’s important that these devices are set up to allow for remote management and monitoring, for ensuring that these devices are up-to-date and secure.
Summary – What should we take away from all of these recent attacks?
With further regulation from the Federal government on the horizon in response to these repeated sorts of privacy breaches, it’s important to make sure you are at least a few steps ahead of the curve. The good news is, as can be learnt from these breaches, a few simple steps can help reduce the likelihood of your business falling victim to the same sort of cyber-attacks.
Speaking generally about the Optus breach, considering what systems are internet facing, and also what protections are in place at the infrastructure level is important - but it shouldn’t be the only protection in place to stop unauthorised access to systems. Ensuring that you also have proper authentication and access control built into your applications, even when there are restrictions in place on who can access those systems built into the infrastructure, could save you from the nightmare that Optus found itself facing.
Implementing two-factor authentication and other standard security policies within your organisation, and more importantly, strictly enforcing compliance – can help stop you from being hit by the same attack that caused Medibank to be compromised. However, proper governance around overall cyber-security should be the real focus here - each organisation should look into establishing sensible policies and procedures around security internally, making sure all staff are aware of and know how to follow them, and that they understand how important they are to the security of the business as a whole.
Finally, by making sure that all staff use work devices and that those devices are monitored and updated - even when working remotely, means that you can further reduce the chances of your business being the next one in the national headlines. From a cyber-security perspective, it’s important to have visibility over the systems that your staff use – as you are flying blind if you can’t ensure that all the devices they're using for work are up-to-date with the latest security patches and have some form of endpoint anti-virus protection.
Overall, heeding the advice of the Digital Rights Watch – which is to only store the information that you require from your users – could prove invaluable. By doing this, should you ever become a victim of such an attack, you can dramatically limit the impact this will have on your customers and your business. Because as they say, less is more, and an ounce of prevention is worth a pound of cure!
Have any questions about how to increase your cyber security?
If you have any questions about specific steps that you can take to improve the security of your systems, reach out to us! You can email us at sales@micron21.com or give us a call on 1300 769 972 (Option #1).
Sources
1, Optus data breach: everything we know so far about what happened, <https://www.theguardian.com/business/2022/sep/29/optus-data-breach-everything-we-know-so-far-about-what-happened>
2, Optus rejects insider claims of 'human error' as possible factor in hack affecting millions of Australians, <https://www.abc.net.au/news/2022-09-23/optus-rejects-claim-hack-likely-result-of-human-error/101468846>
3, Optus Under $1 Million Extortion Threat in Data Breach, <https://www.bankinfosecurity.com/optus-under-1-million-extortion-threat-in-data-breach-a-20142>
4, Optus hack: Hacking community slam Optusdata as a 'script kiddie', <https://www.msn.com/en-au/news/australia/optus-hack-hacking-community-slam-optusdata-as-a-script-kiddie/ar-AA12kEjt?cvid=9cd6926c890542739c93928e135505e9#image=2>
5, Lapsus$: Two UK teenagers charged with hacking for gang, <https://www.bbc.com/news/technology-60953527>
6, What Happens to Stolen Healthcare Data?, <https://healthtechmagazine.net/article/2019/10/what-happens-stolen-healthcare-data-perfcon>
7, New task force to target 'scumbag' hackers following Medibank and Optus cyber attacks, <https://www.abc.net.au/news/2022-11-12/medibank-cyber-hack-optus-data-breach-task-force-afp/101647168>
8, How it happened: Medibank hack came via a single login, <https://www.thesaturdaypaper.com.au/news/politics/2022/11/19/how-it-happened-medibank-hack-came-via-single-login#mtr>
9, Harcourts Melbourne City real estate agency advises customers of data breach, <https://www.abc.net.au/news/2022-11-02/harcourts-melbourne-real-estate-agent-stafflink-data-breach/101608270>
10, Real estate sector data breach could be worse than Optus hack, digital rights advocates say, <https://www.sbs.com.au/news/article/real-estate-sector-data-breach-could-be-worse-then-optus-hack-says-digital-rights-watch/l72rlry1z>
