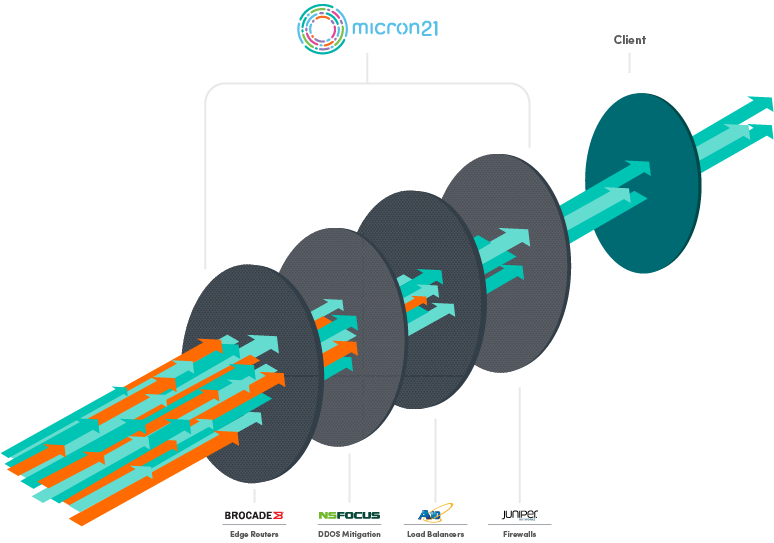
Micron21’s DDoS Mitigation Algorithms and Techniques
Our DDoS mitigation strategies are underpinned by a suite of sophisticated algorithms designed to detect and neutralize threats effectively.
Rigorous Protocol Compliance and Filtering
We perform RFC (Request for Comments) checks to ensure that all network traffic adheres to established internet protocol standards. This helps us identify and discard malformed or malicious packets that deviate from expected behaviors.
Our systems leverage blacklists, Threat Intelligence (NTI) blacklists, whitelists, GEOIP filter lists, and access control lists to allow or block traffic based on reputation and geographic origin.
Advanced TCP and UDP Protection Mechanisms
For TCP traffic, we employ techniques such as regular expression filtering and TCP SYN source IP rate limiting to manage and mitigate SYN flood attacks. We monitor TCP SYN bandwidth limits, perform TCP SYN time sequence checks, and apply TCP fragment controls to ensure the integrity of TCP communications. TCP watermark checks and pattern matching enable us to detect and block sophisticated attack patterns targeting TCP protocols.
In UDP traffic, we implement regular expression filtering and payload checks to scrutinize the contents of packets. UDP fragment control and packet length checks help us identify and mitigate attempts to exploit the UDP protocol. We also utilize UDP traffic control, watermark checks, and pattern matching, along with reflection amplification rules, to guard against reflection and amplification attacks that can overwhelm network resources.
Comprehensive Detection of Diverse Attack Vectors
Our algorithms are designed to detect and mitigate a wide range of attack vectors, including SYN floods, ACK floods, UDP floods, ICMP floods, IGMP floods, HTTP/HTTPS floods, DNS attacks, LAND attacks, SIP floods, and attacks exploiting protocol anomalies such as protocol null and TCP flag misuse. We defend against DNS query and response floods, NTP amplification, SSDP amplification, SNMP amplification, and CHARGEN amplification floods.
By monitoring for private IP abnormalities, traffic anomalies, and utilizing auto-learning baselines, we can detect deviations from normal traffic patterns. Our systems assess regional or IP group inbound and outbound traffic abnormalities, enabling us to respond swiftly to localized threats. False source IP detection helps us identify and block spoofed IP addresses commonly used in DDoS attacks. Integration with Threat Intelligence feeds enhances our ability to proactively defend against emerging threats.
Programmable Protection Rules
Micron21’s platform supports programmable protection rules, allowing for customized mitigation strategies tailored to specific network environments. This flexibility enables us to adapt quickly to new attack methods and to fine-tune defenses based on the unique traffic patterns of each client.
Reporting and Analytics
Micron21 provides comprehensive reporting and analytics to give you full visibility into your network’s security status. We track attack events, provide detailed attack summaries, and analyze traffic trends to offer insights into the nature of threats against your network. Our extensive logging captures data on attack summaries, traffic alerts, performance metrics, link states, and authentication activities.
Our reporting capabilities include both real-time and historical reporting, allowing you to monitor ongoing threats and review past incidents for trend analysis and strategic planning. We offer scheduled reports by email, ensuring that key stakeholders receive regular updates on the security posture of your network. This level of transparency empowers you to make informed decisions about your security strategies and resource allocation.
Compliance and Certifications
Micron21 is committed to meeting the highest standards of compliance and certifications. Each of our scrubbing locations is Information Security Registered Assessors Program (IRAP) certified, meeting stringent Australian government security standards.
As an Australian-owned company, we are not subject to foreign data access laws like the USA PATRIOT Act, ensuring your data remains sovereign and protected under Australian law.
For our European clients, we adhere to the General Data Protection Regulation (GDPR), ensuring data privacy and protection in compliance with European standards. Our commitment to compliance ensures that your organization meets its regulatory obligations while benefiting from our advanced DDoS mitigation services.
Service Offerings
Micron21 offers a range of DDoS Protection service offerings to meet the diverse needs of our clients. Our always-on DDoS protection provides continuous monitoring and instant mitigation of any detected attacks, ideal for organizations requiring uninterrupted service and immediate response times. For businesses with lower risk profiles or budget constraints, our on-demand protection offers flexible activation of mitigation services upon detection of an attack.
Our DDoS Protection services involve traffic redirection, where malicious traffic is diverted to our scrubbing centers, cleaned, and legitimate traffic is forwarded to your destination. This seamless integration has minimal impact on your existing network architecture and is easy to deploy. For website and application protection, our remote protection services provide DDoS mitigation without the need for network changes, using DNS-level redirection to route traffic through our scrubbing centers.
For each of our DDoS Protection services, you can customize the level and type of protection to meet your specific needs, as well as select the preferred level of monitoring and support.
Deployment and Integration
Micron21’s DDoS mitigation services are designed for rapid deployment, with quick setup requiring minimal changes to your existing infrastructure. Our solutions are scalable, tailored to organizations of all sizes—from small businesses to large enterprises. Our team of experts provides guidance on best practices and optimal configurations for your specific needs, ensuring a seamless integration with your network.
Global Network and Connectivity
Our global network and connectivity are key strengths of Micron21’s DDoS mitigation services. We have extensive peering with major ISPs and peering exchanges globally, reducing latency and improving performance. Domestic scrubbing ensures that attack traffic originating within a region is mitigated locally, avoiding unnecessary latency from international routing. Our use of BGP Anycast routing distributes incoming traffic across multiple scrubbing centers for load balancing and redundancy, enhancing the reliability of our services.